usd-2023-0050 | Gambio 4.9.2.0 - Sensitive Data in log files
Product: Gambio
Affected Version: 4.9.2.0
Vulnerability Type: CWE 256 - Plaintext Storage of Password
Security Risk: High
Vendor URL: https://www.gambio.de
Vendor Status: Not fixed
CVE Number: CVE-2024-23760
Description
Gambio is software that is designed for running online shops.
It provides various features and tools to help businesses manage their inventory, process orders, and handle customer interactions.
According to their homepage, the software is used by more than 25.000 shops.
The legacy-error-handler.log.json file contains the cleartext passwords that were set during the installation.
Note: Upon discovery, our team immediately initiated the responsible disclosure process by contacting the vendor behind Gambio.
Unfortunately, despite multiple attempts, our attempts to engage the vendor in resolving this issue have been met with silence.
The vulnerability is still unfixed.
Proof of Concept
The legacy-error-handler.log.json and legacy-error-handler.log.txt files contain the cleartext admin password that was set during the installation.
In addition, the database credentials are also part of the logs.
The file can be requested by administrative users using the web UI.
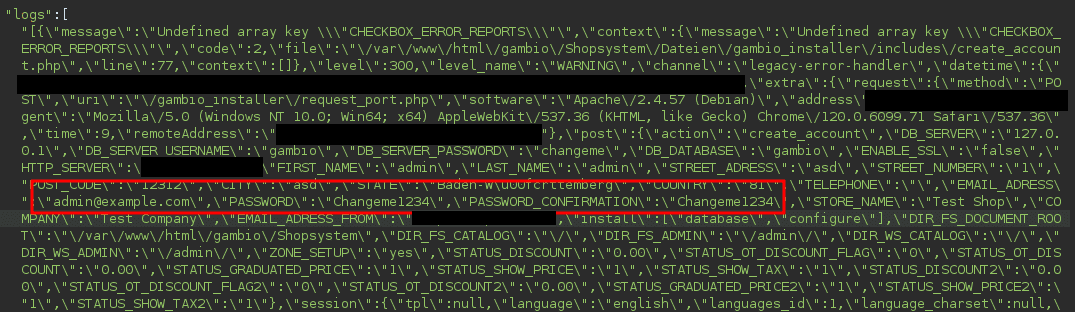
The files are located in the "logfiles" subdirectory of the webroot.
Fix
Do not store credentials in plaintext.
References
Timeline
- 2023-12-08: First contact request via email.
- 2023-12-21: Second contact request via email.
- 2024-01-17: This advisory is published.
Credits
This security vulnerability was identified by Christian Poeschl and Lukas Schraven of usd AG.