usd-2025-58 | Broken Access Control in User Registration
Product: memos
Affected Version: v0.25.2
Vulnerability Type: CWE-862: Missing Authorization
Security Risk: Medium
Vendor: usememos
Vendor URL: https://github.com/usememos/memos
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
CVE Number: CVE-2025-65795
CVE Link: https://www.cve.org/CVERecord?id=CVE-2025-65795
Advisory ID: usd-2025-58
Description
Memos is a lightweight, self-hosted knowledge management and note-taking platform designed for personal use. The architecture features a Go backend paired with a React+Vite frontend, using gRPC for internal communication and providing REST API access through gRPC-Gateway. It supports multiple database backends (SQLite, MySQL, PostgreSQL) and includes features like file attachments, OAuth/SSO integration, activity logging, and internationalization.
Administrative users can disable public user registration. However, unauthenticated users can still be created by direct calls to the REST API.
Proof of Concept
User registrations can be disabled in the application settings, as shown in the following screenshot.
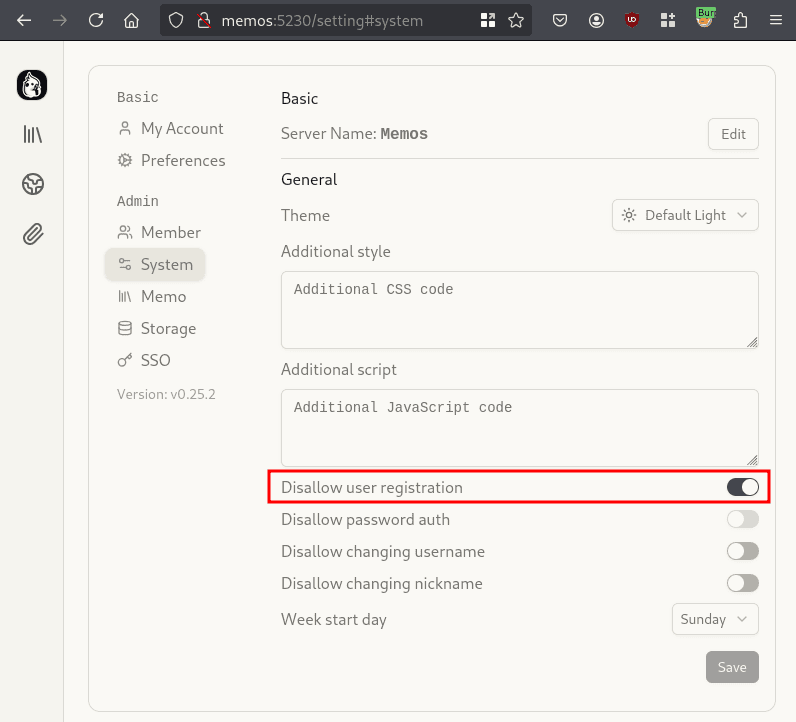
Nevertheless, an account can be created by the following HTTP request to the REST API.
POST /api/v1/users HTTP/1.1 Host: memos:5230 Content-Type: application/json Content-Length: 42 { "username":"Test", "password":"12345678" }
Note that this enables further attacks that require authentication, such as arbitrary file write or account takeovers as shown in usd-2025-56 and usd-2025-57.
Fix
A fix for the vulnerability has been submitted as pull request.
References
Timeline
- 2025-11-03: First contact request
- 2025-11-04: Pull request submitted
- 2025-11-06: Commit merged to main by vendor
- 2025-11-25: Version 0.25.3 was released
- 2025-12-03: This advisory is published
Credits
This security vulnerability was identified by Florian Dewald of usd AG.